Fail2Ban: Protect your web server from bots
I often see in the web server logs, that bots are trying to find valid backend login pages on common url paths. The bot scans multiple endpoints. If a request returns 2xx, it is possible that the login gets bruteforced.
The login paths for WordPress, MySQL UIs, Typo CMS and phpmyadmin are frequently requested. These bots are trying to attack unprotected installations.
What is the reason for this protection?
I recently analyzed my Apache httpd logs (access_log, error_log) and found interesting requests. All of them resulted in 404 Not Found, since I don't have admin endpoints exposed publicly.
[...] /mysql/admin/ HTTP/1.1" 404 [...]
[...] /mysql/dbadmin/ HTTP/1.1" 404 [...]
[...] /mysql/sqlmanager/ HTTP/1.1" 404 [...]
[...] /mysql/mysqlmanager/ HTTP/1.1" 404 [...]
[...] /phpmyadmin/ HTTP/1.1" 404 [...]
[...] /phpMyadmin/ HTTP/1.1" 404 [...]
[...] /phpMyAdmin/ HTTP/1.1" 404 [...]
[...] /phpmyAdmin/ HTTP/1.1" 404 [...]
[...] /phpmyadmin2/ HTTP/1.1" 404 [...]
[...] /phpmyadmin3/ HTTP/1.1" 404 [...]
[...] /phpmyadmin4/ HTTP/1.1" 404 [...]
[...] /2phpmyadmin/ HTTP/1.1" 404 [...]
[...] /phpmy/ HTTP/1.1" 404 [...]
[...] /phppma/ HTTP/1.1" 404 [...]
[...] /myadmin/ HTTP/1.1" 404 [...]
[...] /shopdb/ HTTP/1.1" 404 [...]
[...] /MyAdmin/ HTTP/1.1" 404 [...]
[...] /program/ HTTP/1.1" 404 [...]
[...] /PMA/ HTTP/1.1" 404 [...]
...
This abstract of this file is simplified. It also contains a lot more than this.
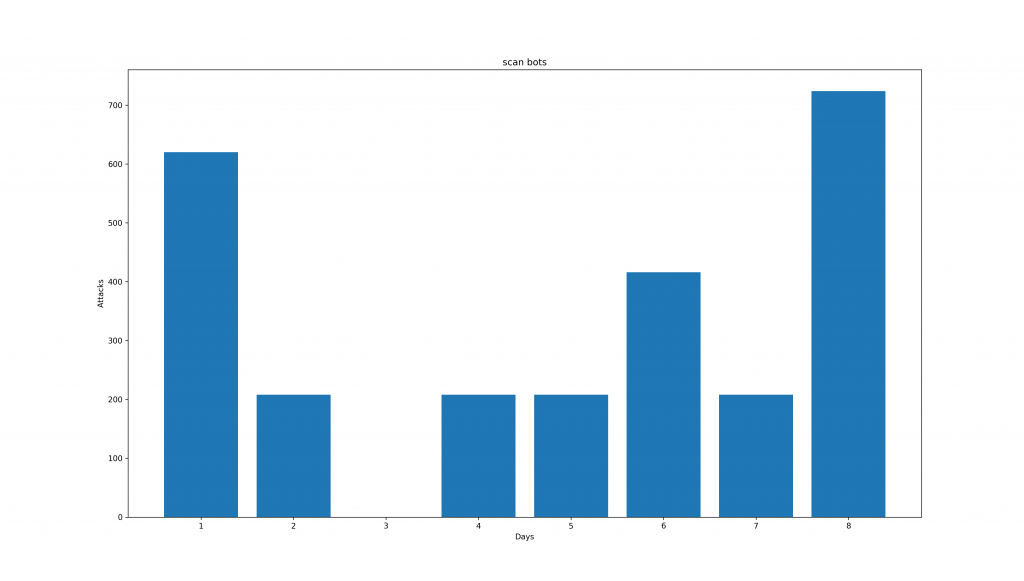
This chart shows the count of this type of scans for each day on readfromfile.com. It's quite interesting to see, that most of the scans are on Sundays (Day 1 and Day 8). During the week, its only half of the amount. A data set of common back-end admin names are probably used. During the 8 days, no detected IP attempts to scan twice in this period.
What is the bot trying to do?
These bots are trying to detect a back-end admin area. After a successful detection, it is possible that this bot will start a bruteforce attack on an admin login panel. If you want to protect your admin area (wordpress, phpmyadmin, typo cms ...) and also your website in general, try to move your admin endpoints to an internal network. If that is not possible, you can use fail2ban.
How can I protect my website?
Is this your first time using fail2ban? Please visit my previous post for an installation guide and general instructions.
If you already installed fail2ban, you are ready to go. Please go to /etc/fail2ban/filter.d.
In this directory are all defined filters for fail2ban. You can easily create a new filter:
vi apache-block-scan-bots.conf
Just Copy&Paste the following code into your new file.
[INCLUDES]
before = apache-common.conf
[Definition]
failregex = (?i)^%(_apache_error_client)s (AH\d+:)? File does not exist: .*$
ignoreregex =
We now have to activate the filter. Just append this at the end of the file jail.local in the parent directory.
[apache-block-scan-bots]
enabled = true
port = http,https
filter = apache-block-scan-bots
logpath = /var/log/httpd/error_log
maxretry = 10
findtime = 60
bantime = 86400 # = 1 day
Feel free to modify maxretry, findtime and bantime.
Test the new configuration with:
fail2ban-client -d
The last step is to reload the fail2ban configuration:
fail2ban-client reload
This configuration will ban every scan attempt (scans resulting in 404 Not Found), if there are more than 10 requests of this kind during 1 minute.
Tested on:
- OS: CentOS 7
- Web server: Apache httpd 2.4.6
- fail2ban: 0.9.6
Credits:
- Post photo by Luke Chesser on Unsplash